RFID on Driver's License
I looked for a short article that covered the info on this short mp3 from CBC radio, but couldn't find it. So listen to the 18 minute mp3 searchengine attachment if your interested in security issues with RFID on Driver's Licenses. It's an interview with Ontario's Commissioner of Privacy and Information.. If you're interested in other podcasts from SearchEngine ( a weekly radio show on the CBC), check here.Who’s afraid of “behavior tracking”?
Posted by Jesse Brown on March 11 at 01:44 PM
Google has announced
some new features for their AdSense network, and a predictable
flood
of horrified
headlines
have followed.
So what are we supposed to be afraid of?
Well, from now on, “interest-based” ads will serve you advertising based on the kind of sites you’ve visited before. Furthermore, “previous interaction” ads will be based on what you’ve done on those sites; to borrow Wired’s example, if you put a camera in your shopping cart but never actually purchased it, expect to see a lot of camera ads in the future.
Am I alone in not worrying about this? “Behavior tracking” does sound scary, but let’s consider a couple of facts:
1. Google isn’t storing or sharing any behavioral information about us. Our histories are saved to cookies that live on our own computers, and even so- names and addresses aren’t included.
2. If it still really bothers you, you can opt out.
So who cares?
Actually, I do: I like these features.
Online ads need to get a lot better if the current economic model of the web is to survive. We expect wonderful online tools and content for free, which means this stuff must be supported by ads. Typically, by lousy ads- irrelevant, annoying, and ignorable ads.
If I have to live with advertising, I’d prefer it be relevant advertising. Knee-jerk privacy scares say moreabout techphobia than about big-brother intrusions, and they cloud our thinking about true privacy worries.
For example: Google’s bug last weekend that allowed unauthorized users access to people’s Google Doc files. Though damage control was swift, this was a major foul-up. Cloud computing is a public trust, and this can’t happen again. Let’s save our outrage for incidents like this.
Trial by Jury is broken.
Posted by Jesse Brown on March 18 at 11:53 AM
Last month in a Swedish courtroom, a minor historical event took place
in under 140 characters. “EPIC WINNING LOL” went the message,
announcing that half of the copyright infraction charges against The
Pirate Bay torrent tracker site had been dropped.
It wasn’t the first Twitter message to emit from a courtroom, but as far as I can tell, it was the first “tweet” to come from a defendant at his own trial- the Pirate Bay's Peter Sunde. (link)
Now, The New York Times reports on other cases of mobile devices disrupting the courts. A recent federal drug case in Florida became a mistrial when it was revealed that 8 of the 12 jurors had been researching it online, against court orders. Other instances of the same are popping up.
This is a big threat to the whole idea of trial by jury. From the Times piece:
…the rules of evidence, developed over hundreds of years of jurisprudence, are there to ensure that the facts that go before a jury have been subjected to scrutiny and challenge from both sides…
Sounds good to me. But I have to ask: how can the courts possibly control this?
Some judges ban cellphones and PDAs in the courtroom, but once court’s out of session, Google’s waiting. Short of sequestering each and every jury in wireless hotel rooms (an expensive proposition that makes jury duty sound like prison) it seems that this is just another old system that the Internet has broken.The existence and operation of massive, coordinated, government-affiliated online espionage networks is typically the province of television or the silver screen, rather than the subject of research. In the real world, even a direct link between online and offline action (Russia's invasion of Georgia and the simultaneous online attacks against that country are a good example) is not enough to automatically prove that the government behind the one is automatically behind the other. We've covered the rise of hacktivism previously on Ars; as more citizens come online, we'll undoubtedly see more of this type of crowdsourced aggression in the future.
Researchers in Toronto, however, may have actually discovered and tracked a hacking effort that can be traced back to a foreign intelligence network—China's, in this case—over the past ten months. The team, which is affiliated with the Munk Centre for International Studies, has published an extensive report on the activities of what they dub GhostNet. Their investigation took place from June 2008 through March of 2009, and focused on allegations that the Chinese had engaged in systemic online espionage activities against the Tibetan community. GhostNet was spread through the use of a wide variety of Trojans, many of which were controlled through a program nicknamed gh0st RAT (Remote Access Tool).
The report can be read (PDF) in one of two ways: either as a primer on the operation and capabilities of both the gh0st RAT tool and the GhostNet network, or as an intelligence document detailing (with some redactions) where GhostNet infections were found and, perhaps more importantly, where the espionage network's C&C servers appear to be located. For the purposes of this discussion, we're going to focus more on the sociopolitical implications of GhostNet and less on the technical details. It will have to suffice to say that gh0st RAT is apparently a complex and nasty bit of business that does not rely on the successful installation of one particular Trojan in order to operate.
Its various payloads appear to have been delivered using standard social engineering and/or spear phishing techniques. This could be seen as further proof that relatively simple attack vectors are sufficient to overwhelm the security training and/or antivirus software of high-level government institutions; many of the targets GhostNet infiltrated should never be susceptible to a gussied up version of a social engineering attack.
Just because you're paranoid...
China has been accused of attacking a number of groups and institutions through the use of cyber espionage, a fact which already put it high on the research team's "countries of interest" list. The team's investigation ended up focused on Tibet in particular "because of the unprecedented access that we were granted to Tibetan institutions through one of our researchers and persistent allegations that confidential information on secure computers was somehow being compromised." The report notes that the lead field researcher had a substantial history of working with the Tibetan community, and was able to secure access to "the private office of the Dalai Lama, the Tibetan Government-in-Exile (TGIE), and a number of Tibetan non-governmental organizations" (NGOs).
The group's on-site research identified infected systems within the Office of His Holiness the Dalai Lama (OHHDL), the network of the TGIE, and the offices of a Tibetan NGO, TibTec. In the latter's case, there was already anecdotal evidence of espionage within the Drewla Initiative Project. According to its description, "Drewla ('connection' in Tibetan) is an online outreach project...that employs Tibetan youth with Chinese language skills to chat with people in mainland China and in the diaspora, raising awareness about the Tibetan situation, sharing the Dala Lama's teachings, and supplying information on how to circumvent...government censorship on the Internet."
This is rather obviously the sort of project the Chinese government would be less than fond of. The anecdotal evidence we mentioned is given on page 29/53 of the PDF, which tells the story of a young member of Drewla who was returning to her family in Tibet after two years away. She was detained at the Nepalese/Tibetan border and held for two months. Accused of participating in the Drewla Initiative, "She denied having been politically active and insisted that she had gone to Dharamsala for studies. In response...the intelligence officers pulled out a dossier on her activitiies and presented her with full transcripts of her Internet chats over the years. They indicated that they were fully aware of, and were monitoring, the Drewla outreach initiative."
...doesn't mean they aren't out to get you
GhostNet is extremely selective for a malware network. The Toronto researchers listed the following systems as ones they are highly confident have been compromised:
- ASEAN (Association of Southeast Asian Nations)
- Asian Development Bank
- Associated Press, UK
- Consulate General of Malaysia, Hong Kong
- Department of Foreign Affairs, Indonesia
- Department of Foreign Affairs, Philippines
- International Campaign for Tibet
- NATO (SHAPE HQ)
- Office of the Dalai Lama, India
- Russian Federal University Network, Russian Federation
- Students for a Free Tibet, US
- Taiwan Government Service network, Taiwan
- Tibetan Government in Exile, India
Ommitted from that list is any mention of the dozen-plus embassies believed to be infected across Southeast Asia or in other geographical areas of interest to China. As the authors themselves point out, there are plausible explanations for GhostNet that do not require it to be an espionage tool of the Chinese government, though they think that this explanation is both the most obvious and "the one in which the circumstantial evidence tilts the strongest." The fact that the attack IPs examined resolve back "in at least several instances to Hainan Island, home of the Lingshui signals intelligence facility and the Third Technical Department of the People's Liberation Army" definitely helps this case.
Alternatives must, however, be considered. These include the possibility that GhostNet is essentially a fluke, a deliberate creation of a foreign power other than China (but with a similar set of interests), or the creation of a group searching for information to sell at a profit. This last option is most plausible if we consider the likelihood that there are many GhostNets in operation around the world, each designed to monitor its own particular interests. As the authors note, they "can safely hypothesize that it [GhostNet] is neither the first nor the only one of its kind."
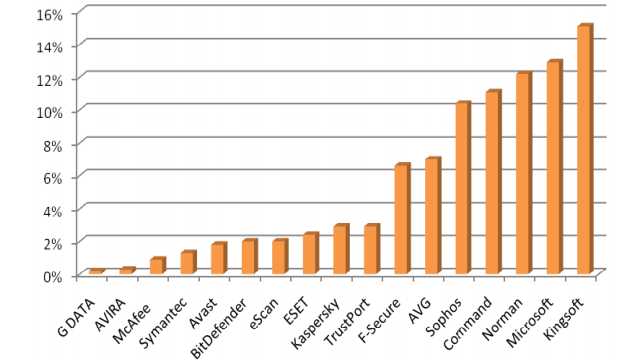
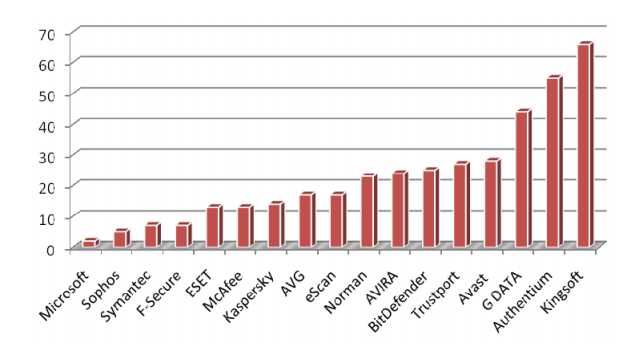
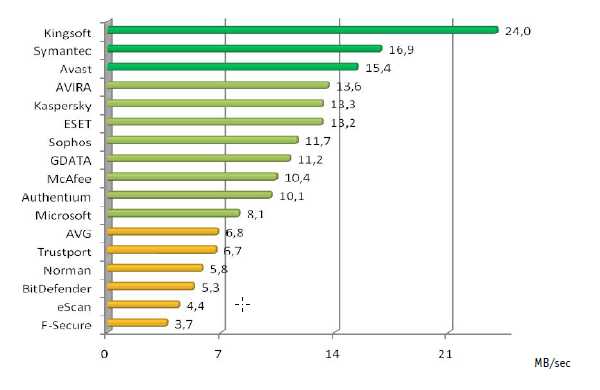
AV-Comparatives February 2009 report: four winners
AV-Comparatives' November 2008 report has arrived. There are two unsurprising winners and two winners who look like they're finally back in the game.
http://www.networkworld.com/news/2009/032709-firefox-likely-to-win-race.html
FWIW - I had to remove some spyware from this article. Mostly embedded doubleclick stuff. This happens occasionally when I cut and paste an article, so its sometimes useful to notice the sources of these articles. It's nice that avast lets me know when these things are in my email! This was from Network World -SH
Firefox likely to win race to fix PWN2OWN contest bug
Unless its two biggest rivals take extraordinary steps, Mozilla will be the first browser maker to patch a critical vulnerability used a week ago to win $5,000 in a hacking contest.
Browsers get hacked before phones at security show
At the PWN2OWN competition last Thursday, a computer science student from Germany who would only give his first name as Nils cracked a Sony laptop running Windows 7 by exploiting a previously unknown bug in Microsoft Corp.'s new Internet Explorer 8 (IE8). Nils quickly followed that hack with two more, of Apple Inc.'s Safari and Mozilla's Firefox, both running on a MacBook.
For each successful exploit, Nils was paid $5,000 -- a total of $15,000 -- by contest sponsor 3Com Corp.'s TippingPoint. He also was awarded the Sony Viao notebook for being the first researcher to hack the machine.
By the rules of PWN2OWN, researchers are not allowed to divulge details of their vulnerabilities and exploits, but instead sign over the rights to both to TippingPoint, which in turn reports the bugs to the appropriate vendor.
Earlier today, Mozilla's director of security engineering, Lucas Adamski, told IDG News reporter Robert McMillan that Firefox would be patched against a critical vulnerability that had been disclosed on the milw0rm.com site yesterday.
Later in the day, Mozilla added that it would also fix the bug Nils revealed. "Both issues have been investigated and fixes have been developed which are now undergoing quality assurance testing," the company announced in a post to its security blog this afternoon. "These fixes will be included in the upcoming Firefox 3.0.8 release, due to be released by April 1."
Mozilla has labeled the 3.0.8 update as a "high-priority fire drill security update;" in other words, an emergency patch. Before declaring the fire drill update, Mozilla had slated 3.0.8 for a mid-April release.
It's unlikely that either Microsoft or Apple will patch their browsers' bugs before Mozilla. Apple, for example, never generates Safari patches within such a short time span. For that matter, neither does Microsoft.
The IE flaw, however, may already be fixed -- at least in IE8. The PWN2OWN contest featured the release candidate of IE8, which is the version Nils hacked. Several hours before the contest kicked off, Microsoft released the final edition of IE8, which some have speculated included a fix for Nils' bug.
They point to ZDNet security blogger Ryan Naraine's interview with Nils, during which he said he "really appreciated" the work of Mark Dowd and Alex Sotirov, two researchers who announced last summer that they were able to circumvent Windows Vista-specific security measures designed to hamper attacks. Yesterday, Dowd confirmed that IE8's final build addresses his and Sotirov's tactics "completely."
It's not known, however, if versions of IE prior to IE8 are also vulnerable to attack. In his interview, Nils admitted only that he had not been able to trigger the bug in IE7.
If Mozilla follows past practice, it will release Firefox 3.0.8 next Wednesday in the afternoon Pacific time, at which point users will be able to download it directly from the Mozilla site or use the browser's built-in updater to download and install the patched version.