Hackers seize on 0-day flaw in Microsoft's
PowerPoint
Independent security company Secunia has rated the
PowerPoint vulnerability 'extremely critical,' its highest-risk ranking
sh- I guess this means not to read
forwarded powerpoint files - also not to forward them!Microsoft warned Thursday that hackers are actively exploiting a software vulnerability in PowerPoint, the company's presentation application.
Choosing the Right Hardware and Software for Data Protection Solution - read this white paper.
There's no patch yet for the bug, which could allow an attacker to completely control a computer. It affects Office 2000 Service Pack 3, Office XP SP3, Office 2003 SP3, and Office 2004 for Mac, Microsoft said in an advisory. Office 2007 is unaffected.
Microsoft said it has seen limited, targeted attacks. The Danish security company Secunia ranked the problem as "extremely critical," its most severe rating.
Secunia said the vulnerability "is caused due to an unspecified error that may result in access to an invalid object in memory when parsing a specially crafted PowerPoint file."
Microsoft advised users to not open or save Office files that come from untrusted sources. If the file is opened, users won't have much of an indication that it's a malicious file.
"Usually, these files look legit when opened, so it is quite easy to fall prey and not even notice that something malicious ran in the background," according to a post on the company's Malware Protection Center blog.
Hackers frequently hunt for vulnerabilities in commonly used software products, as it's another avenue other than the operating system to infect a computer with malicious software.
To be hacked, a user would either have to download a malicious file hosted on a Web site or open a file sent through e-mail, Microsoft said.
Microsoft has added a signature that will block access to PowerPoint exploit files in its Windows Live OneCare and Forefront Client security products. The signature is included in definition update 1.55.975.0 or higher.
The company noted that the exploit files have been recently submitted to VirusTotal, a Web site that aggregates antivirus engines.
Malware can be submitted to see which security products detect it. The site is often used by hackers to determine if their malware will be blocked by certain security software.
03 April 2009
Conficker worm strikes 4 percent of PCs
Security experts at IBM have said that the impact of the Conficker.C worm may be higher than previously thought.
Although Conficker is clearly the worst worm outbreak in years, the results came as a surprise, according to Holly Stewart, a threat response manager with ISS. "It is higher than what we expected; I thought we'd see 1 to 2 percent," Stewart said.
Late last week, IBM researchers reverse-engineered Conficker and figured out a way to track infections by measuring peer-to-peer traffic on the network. They used that technique to reach their estimate.
The results are similar to numbers released earlier this week by OpenDNS, which said it had also spotted a much larger number of infections than expected. Both IBM and OpenDNS' numbers count Conficker.C, the latest variant of the worm, and one that is easier to spot communicating on the network.
Conficker began spreading in October 2008, using a handful of sneaky tricks to spread. Once it infects a machine, it can spread very quickly on a local area network by taking advantage of a now-patched flaw in Microsoft Windows.
Experts had pegged Conficker infections in the 2 million to 4 million range, but IBM's numbers suggest that they may be much higher than that, perhaps in the tens of millions.
Still, Stewart cautioned against concluding that 4 percent of Internet users had been infected. "It's not a perfect number, nothing is. But it's the best that we can give with the data we have right now."
It's possible that Conficker infections are approaching 4 percent, said Danny McPherson, chief security officer with Arbor Networks. Because Conficker is more likely to infect certain types of users - broadband consumers are generally more vulnerable than enterprise or government users, for example - estimates like ISS' could come from a sample that does not represent the Internet as a whole, he said.
Still, by any measure, Conficker is a big problem. "Even if they're off by an order of magnitude - which is possible - the number of infected machines is immense."
03 April 2009
IE continues to lose ground to Firefox
Life is getting increasingly tough for Microsoft's Internet Explorer, which four years ago was running on nearly nine out of 10 computers. As of last month, just two out of every three users surfed the Internet using IE, a web metrics company has found.
IE lost 0.7 of a percentage point to end March with a 66.8 percent share of the browser market, the lowest number since Net Applications began tracking browsers in 2005. The launch of IE8 two weeks ago didn't stop or even slow Microsoft's slide; the browser's March drop was slightly larger than the average loss during the previous 12 months.
Earlier data from NetApp indicated that in IE8's first full week of availability, users of rival browsers weren't persuaded to switch. The Microsoft browser was instead downloaded and installed by people who had been running IE7.
In the past year, IE's share has slipped 8 percentage points. If the current rate of decline continues, Microsoft's share will fall below 60 percent in January 2010, the company's publicly stated delivery date for the Windows 7 operating system.
As has generally been the pattern, IE's March losses were countered by rival browsers' gains. Mozilla's Firefox increased its share by the largest amount, 0.3 percentage points, while Apple's Safari and Google's Chrome grew by 0.2 and 0.08 percentage points, respectively.
Firefox, which as of March had six consecutive months of growth, ended March with 22 percent of the browser market, a record for the open-source browser. The beta of Firefox 3.5 - numbered 3.1 until a recent name change by Mozilla - accounted for about 6 percent of all Firefox browsers in use last month, more than double the percentage of IE users running the now-finished IE8.
DNA False Positives
A story about a very expensive series of false positives. The German police spent years and millions of dollars tracking a mysterious killer whose DNA had been found at the scenes of six murders. Finally they realized they were tracking a worker at the factory that assembled the prepackaged swabs used for DNA testing.
This story could be used as justification for a massive DNA database. After all, if that factory worker had his or her DNA in the database, the police would have quickly realized what the problem was.
Exposing Microsoft Windows 7 User Account Control (UAC)
Taking a look at the old and new UAC technology to determine if you should consider Windows 7 and UAC. |
|
Introduction
If you have not heard about User Account Control (UAC) yet, then you need to spend a little time in the archives and blogs surrounding Windows Vista and 7. UAC was first introduced with Windows Vista and ever since has been one of the most debated, talked about, and controversial technologies surrounding post Windows XP desktops. For administrators, UAC is one of the primary reasons Windows Vista is not running for the desktop operating system. For end users, UAC never quite lived up to the marketing and potential that was first generated by Microsoft around the technology. Now that we have nearly seen the full cycle of Windows Vista (yup, it was short lived and not all that glamorous), the next generation, Windows 7, is being tested, evaluated, and criticized for the implementation of UAC that it contains. Here we will look at the old and new UAC technology to determine if you should consider Windows 7 and UAC.
UAC, what it was designed to do
UAC was originally supposed to fix the issue surrounding applications that required administrative privileges, forcing end users to be configured as local administrator. In the beginning, UAC was actually referred to as LUA (Least Privilege User Access), but soon was changed due to the fact it did not come close to solving the issue.
In the final product, UAC is a security related technology that is designed to protect the operating system files and Registry from malicious malware, viruses, and code trying to update the protected areas of the computer. This malicious software attempts to add, modify, and delete key parts of the operating system in an attempt to control the computer and not be noticed.
How UAC Works
UAC (for both Windows Vista and 7) works in a similar manner. There are some changes to Windows 7 that are not included in Windows Vista, but we will look at these in a minute. What UAC does is strip away any “administrative” power from applications, tasks, features, or actions that a user performs during routine functionality. There are really two different modes that UAC can apply to, for a user that has membership in the local Administrators group and a user that does not have membership in this group.
If we look at how Windows Vista UAC works, we will then be able to make the comparison to how Windows 7 UAC is different. We need to look at both modes of operation to see how each works. First, let us look at when a non-Administrator is logged in. In this case, the user has not administrative credentials at logon, so any application, task, or feature will fail to run if it requires administrative privileges. When UAC is enabled (by default to prompt for consent) a dialog box will appear giving the user the ability to input a username and password of an account that has administrative privileges. If credentials are input, then only the application, task, or feature that UAC flagged and prompted for will be elevated to have administrative privileges. Figure 1 illustrates the UAC prompt for consent.
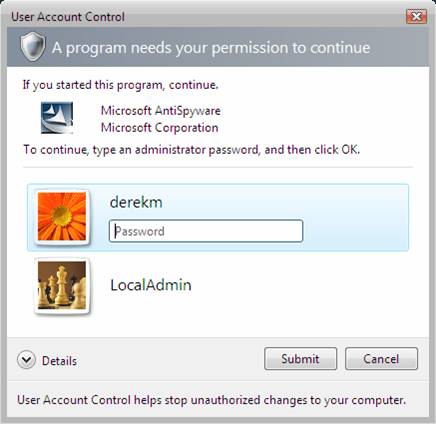
Figure 1: UAC Prompt for Consent dialog box for a standard
user
Next, we need to investigate UAC on Windows Vista for when an “Administrator” is logged in. In the situation where a user is logged in with administrative privileges, UAC in essence strips away all of administrative privileges until a task requires it. This is done such that background apps, viruses, malware, worms and so on, can not modify the operating system files and registry using the logged in credentials. If we look at an authentication token of a user account that has logged in with membership in the Domain Admins group, you can clearly see that the “administrative privileges” have been stripped away. Figure 2 clearly shows how the Domain Admins group SID has been set to “DENY” for the token.
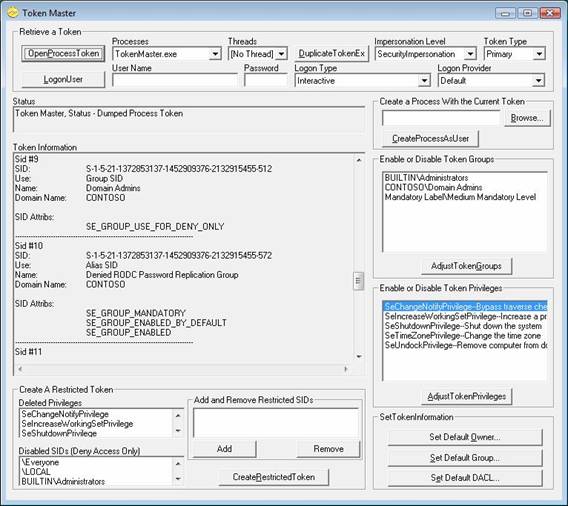
Figure 2: UAC sets the Domain Admins group SID to Deny
permissions on the token
This is the most important aspect of UAC for when an administrator is logged in. Since nearly all malicious applications are written to take full advantage of the currently logged on credentials, the applications will fail! Of course the negative to this is that when ANY application, even those that are well known and run often, are launched, there will be a prompt for consent to run the application. This prompt can be seen in Figure 3.
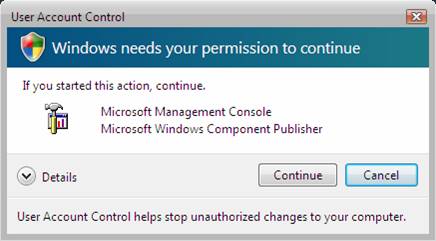
Figure 3: UAC can prompt users for consent if they have
administrative privileges
This can be annoying after the tenth time you run an application that you know is safe. However, security has never been easy or not without hassle. The benefit is that when that malicious application does try to make a touch to a protected file or registry entry, a prompt will appear, indicating to you that something is going on in the background, which you did not initiate.
This behavior for both non-administrators and administrators is when UAC is in the most secure mode, which is to prompt for any task that requires administrative privileges. Anything less than this level of prompting does not protect the computer from malicious applications or viruses, since the background activity would not be noticed and would be allowed to change the system.
UAC Options with Windows 7
The way that UAC functions with Windows Vista has caused many administrators and companies (for non-administrators) to stay away from Vista. With all of this lack of revenue Microsoft was forced back to the drawing board to fix the perceived “annoying” pop-ups that are associated with UAC. The solution that Microsoft came up with in Windows 7 is called the UAC slider.
The slider control allows the administrator of the computer to control which level of UAC prompts, and security, will be implemented. The slider controls which application “types” will cause a prompt and which ones will be allowed to elevate without a prompt. There are a total of four different slider settings, which can be seen in Figure 4.
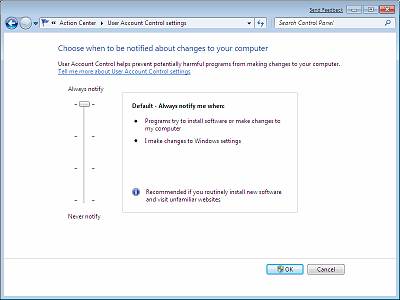
Figure 4: UAC slider in Windows 7
The different levels are defined as follows:
- Always notify on every system change. This is Vista behavior – a UAC prompt will result when any system-level change is made (Windows settings, software installation, etc.)
- Notify me only when programs try to make changes to my computer. This setting does not prompt when you change Windows settings, such as control panel and administration tasks.
- Notify me only when programs try to make changes to my computer, without using the Secure Desktop. This is the same as #2, but the UAC prompt appears on the normal desktop instead of the Secure Desktop. While this is useful for certain video drivers which make the desktop switch slowly, note that the Secure Desktop is a barrier to software that might try to spoof your response.
- Never notify. This turns off UAC altogether.
For most that I have spoken with about this, they feel that the slider, and all but the most secure setting of level 1, is a good alternative. However, all but the most secure setting, level 1, has been hacked! I do not want to go into the hack and Microsoft position here, but you can read all about it by clicking on this link.
So, with Windows 7 you will have a slider to control whether you have a Windows Vista type UAC prompt environment or non-prompting environment. The most secure setting is annoying, but very secure. The non-prompting environment basically turns your Windows 7 computer into a Windows XP computer, which begs the question… why even upgrade if you do not care about security!?
Summary
Windows Vista is more secure than Windows XP due to the benefits that UAC provides. If you don’t prompt or disable UAC, the computer is not much better off than Windows XP. If you run Windows 7 in any mode other than the most secure UAC mode, you are working with the same security as you did with Windows XP. Security has never been easy or convenient. If you decide to disable the great security feature of UAC or dial it down with the slider, you are missing the best security that Windows desktops offer today. If security is not an issue, why even upgrade?? Save your money for when the next version of ConFlicker attacks your computer, you will need it!